When working with Stambia DI, you may have to work with certificates.
For instance, when securing Runtime communication, or when connecting to a secured Runtime, you may need to work with certificates for authenticating the communications.
In Java world, certificates are handled through Java keystores, which you will learn to create and modify in this article.
About this article
This article is dedicated to the creation and edition of a Java keystore which will contain the private and / or public certificates which you may need when working with Stambia DI.
For instance, if you want to secure RMI / HTTP Runtime connections with TLS, you will have to create a Java keystore which will contain the corresponding certificates to authenticate and encrypt communications.
You may also need certificates in various cases such as when trying to communicate with servers using private auto-generated certificates.
About certificates
When you want to communicate with Runtimes secured through TLS, for instance when you communicate with RMIS or HTTPS, you may need to configure the client with the corresponding public certificate.
Certificates are used to authenticate the requests and make sure the communication are encrypted.
This article is focused on how to create a keystore, and how to import public certificates inside.
About keystores
In Java programs certificates are stored in files called 'keystores'.
Once you have retrieved the public certificate to be used, you have to create a keystore and add inside this certificate.
Clients which need to connect can then be configured to use this keystore file.
Creating a keystore
The first step is to create a Java keystore if you do not already have one.
For this, first make sure that Java is installed on your system, as we are going to use a Java tool to create it.
Then, start a command prompt and use the following command to create a keystore with a default dummy key.
Command syntax
keytool -genkey -alias <dummykey> -keystore "<path to keystore>/<keystore file name>.jks"
Example
keytool -genkey -alias dummykey -keystore "D:/keystores/keystore.jks"
When doing this, it will ask to enter a password for the keystore.
Remember this password as you will need it when you need to access the content of the keystore.
It will ask also some other information for the dummy key created, you can define some values in.
The keystore is now created, with a dummy key inside.
The keytool command does not allow to create an empty keystore, that's why you need to create it with this dummy entry.
After having created the keystore, you can delete the dummy key now if you want with the delete option of the keytool utility.
Importing certificates in a keystore
When you have a Java keystore created, you can start importing inside the certificates inside.
There are two types of certificates which can be imported: private keys which are used on server side, and public keys which are used on client side to connect to a server.
Depending on what you want to use the keystore for, you will import the corresponding keys.
The command to import a key is the following:
keytool -import -alias <alias name for the key> -file <certificate file> -keystore <path to keystore file in which to import the certificate> -storepass <password of keystore file>
Example
keytool -import -alias SelfSignedKey -file certificate.cer -keystore keystore.jks -storepass password
About private key
A private key is required most of the time on server side, when you want to secure some services.
For instance, if you want to secure a Runtime with TLS, the Runtime will need to be configured with a keystore containing a private key / public key pair.
About public key
A public key is required most of the time on client side, when you want to connect to some secured services.
For instance, if you want to connect to a Runtime which has been secured with TLS, you will need the corresponding public key on client side.
As an example, Stambia DI Designer will need to know the public key to be able to connect to a Runtime secured, so it will need a keystore in which the corresponding public key is imported.
Troubleshooting
If you encounter issues while performing, with errors messages "cannot recover key", you have probably multiple keys with multiple passwords. Or the key password is different from the keystore password.
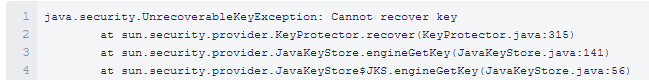
Currently, it is no possible to have a key with a password different from the keystore password.
Java keyManager cannot handle the case where the key does not have the same password as the keystore.


